As software companies, we think we’re safe by chasing the “security carrot”. In reality, it’s our own tools that are leaving us vulnerable.
July 15th, 2020: The Breach
My co-worker Dan and I were meeting over a FaceTime call. Our discussion items were finished but we were talking about random, off-topic rants that we had on our chest (as our meetings usually go).
Just as we’re about the end the call, I glanced over at my other monitor. Dan was in mid-sentence when I darted through, “Holy crap. What the hell?”
“– What?”, Dan replied.
“Bill Gates just got hacked. Wait… did he? It’s coming from his validated Twitter handle”, I responded. I took a screenshot and sent this over to Dan via instant messaging.
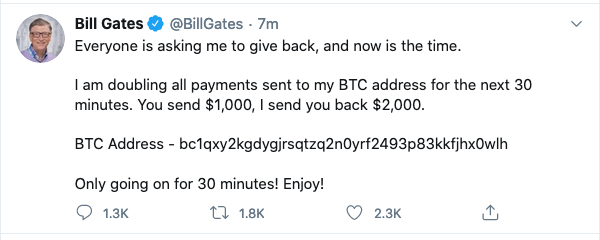
“There’s no way that Bill Gates would tweet this”, I added with a lot of speculation.
Looking at my screen with confusion, I started getting concerned with how fast this tweet was spreading. The numbers of hearts and retweets kept climbing as my screen updated in real-time.
I copied the Bitcoin address and pasted it into Twitter’s search. The entire screen was filled almost the same tweet from various accounts. I then saw Apple’s Twitter account appear and watched many other validated Twitter accounts send out the same thing.
In a serious tone, I said “Dan, there is something very wrong with Twitter. This is not good at all.”